Email Security
Do you send your business letters, love letters, etc. written on postcards? No? Sure, you don't?
Emails are nothing more that electronic postcards. They are transmitted in plaintext passing computers and networks that neither are known by the sender nor the recipient.
That does not mean that every email is caught and read and perhaps changed by someone you don't want to do that. But it is possible and might happen. So anyone that uses emails should think about the risks and the security of his data. On the other hand it is possible to overcome these risks by use of cryptographic methods. But what are these risks mentioned?
- Confidentiality: keep your data private → encrypt the email
- Integrity: prevent changes to your email → electronically sign the email
- Authenticity: Proof of the origin of an email → sign the email
Encryption
Since a long time there exist so called symmetric encryption algorithms. When using them the sender of an email chooses a password to encrypt the message. The recipient of the mail has to use the same password to decrypt the message. The problem is to transmit the password from the sender to the recipient without using insecure communication (e.g. another email). If an attacker get to know the password he can read the encrypted message and neither sender nor recipient would notice that.
Since the invention of asymmetric cryptographic algorithms no one has to worry about the key (password) exchange anymore. The asymmetric algorithms use one key to encrypt a message and another one to decrypt it. One of the keys will be declared as the public key while the other key becomes the private key. The public key - as its name suggests - is published while the private key is kept as a secret by its owner. So if someone wants to send a message to someone else he must use the recipients public key to encrypt the message. The recipient then uses his private key (that only he knows) to decrypt it.
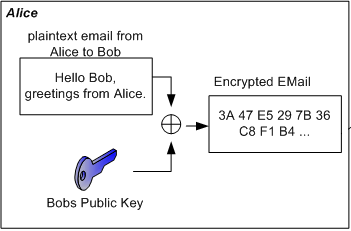
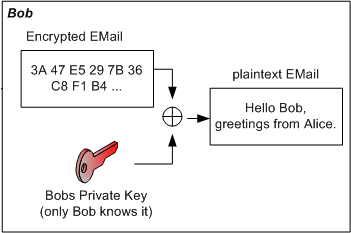
Signature
If you get an email encrypted with your public key, you can be sure that no one else could have read this message as long as your private key is secure. But how do you know that the email is really from the one that is indicated as the emails sender? Perhaps an attacker has caught the email, has written a new email with other content and has encrypted it with your public key. You might not notice this. But you can prevent this by using a mail signature.
For signing an email, the sender calculates a checksum of the emails contents. A checksum is a large number that has a few important qualities. If you change the emails contents only a little bit the checksum will be totally different. In addition it is very difficult (nearly impossible) to find another email that has the same checksum. And if you know the checksum of an email you cannot gather any information about the content of the email. A well known algorithm to calculate checksums e.g. is called MD5 (Message Digest 5).
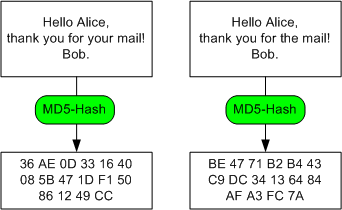
This checksum now is encrypted with the senders private key. When the recipient gets the email he can decrypt the checksum with the senders public key. Then he can compare this checksum with a checksum calculated by himself. If the checksums differ, the email might have been altered. Or the email has not been sent by the one that is indicated as the sender. Then you would have decrypted the checksum with the wrong public key what results in something similar to a random number.
Because the private key that was used to encrypt the checksum is only known to its owner, you can be sure that the identity of the sender has not been faked.
Certificates
Now there is only one point to make email communication really secure. There is no cryptographic method to ensure that someone generates a key pair in the name of someone else. If an attacker would create a key pair for some bank and get the banks customers to use this key, he would be able to decrypt messages that go to the bank (in contrast to the bank that can not decrypt this emails). That makes it important to get a secure and trustworthy mapping between a person and its keys. And for this purpose email certificates are designed.
Certificates are nothing more than a key pair (public und private key), that is signed by a trustworthy organization called Certificate Authority (CA). This organization confirms that the owner declared inside the certificate is really the one that owns the private key.
Unfortunately, most organizations take much money for creating a certificate. But there are alternatives like e.g. CACert.org that are free of charge.
When applying for a certificate you should keep a few things in mind. You should get information about how a CA ensures that the person mentioned in the certificate and you yourself are the same person. Often this is done by a face to face meeting and verification of an identity document like your passport.
Another point to mention is to check if the root certificate of the CA is distributed with most standard software (like Internet Explorer, Firefox, etc. ) because for validating the signature that the CA has made to your certificate the CAs public key must be known. The public keys of most commercial CAs are installed with standard email applications or browsers. When you have got a certificate free of charge this root certificate might be missing and recipients of your signed emails cannot check the validity of your signature. They have to download the root certificate from the CAs website before.
Links
- Thawte: Commercial CA that offers personal email certificates free of charge
- CACert.org: A free CA
- Explanations of the Thawte Web of Trust
- [Christian Barmala Free CA]: A free CA that can be used for the first experiments with email certificates.
- [The Open Source Public Key Infrastructure Book]